Preventing Man In The Middle Attack - 1) intercept the data that is passing between their two targets and 2). One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?.
What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2). One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use.
One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2).
Man in The Middle Attack PDF Computing Service Industries
1) intercept the data that is passing between their two targets and 2). One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?.
Executing A ManInTheMiddle Attack PDF Information And
What are the various techniques, types of attacks, and how to prevent and protect against them?. One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. 1) intercept the data that is passing between their two targets and 2).
What is Man in the Middle Attack? Resmo Cyberpedia
One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2).
Man in the Middle Attack Download Scientific Diagram
One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2).
What Is A ManInTheMiddle Attack? Wiz
What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2). One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use.
Man in the Middle Attack Everything You Need To Know
One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2).
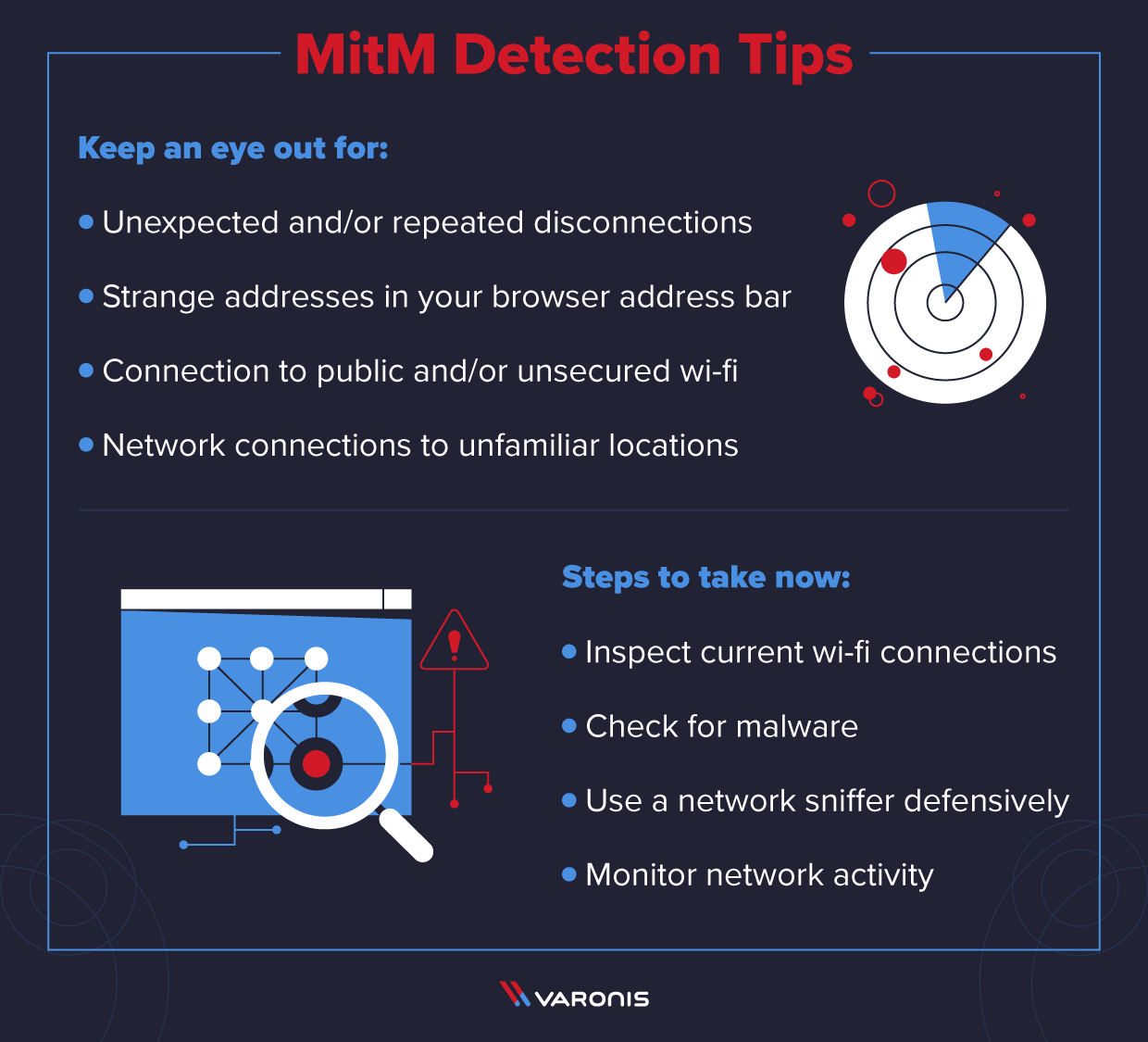
What is a ManintheMiddle Attack Detection and Prevention Tips
One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use. What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2).
What is a ManintheMiddle Attack? How do you prevent one?
What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2). One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use.
Maninthemiddle Attack. Download Scientific Diagram
1) intercept the data that is passing between their two targets and 2). What are the various techniques, types of attacks, and how to prevent and protect against them?. One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use.
What is a ManintheMiddle Attack Detection and Prevention Tips
1) intercept the data that is passing between their two targets and 2). What are the various techniques, types of attacks, and how to prevent and protect against them?. One of the most prevalent mitm attacks involves a bad actor setting up an unsecured wifi hotspot that is free for public use.
One Of The Most Prevalent Mitm Attacks Involves A Bad Actor Setting Up An Unsecured Wifi Hotspot That Is Free For Public Use.
What are the various techniques, types of attacks, and how to prevent and protect against them?. 1) intercept the data that is passing between their two targets and 2).