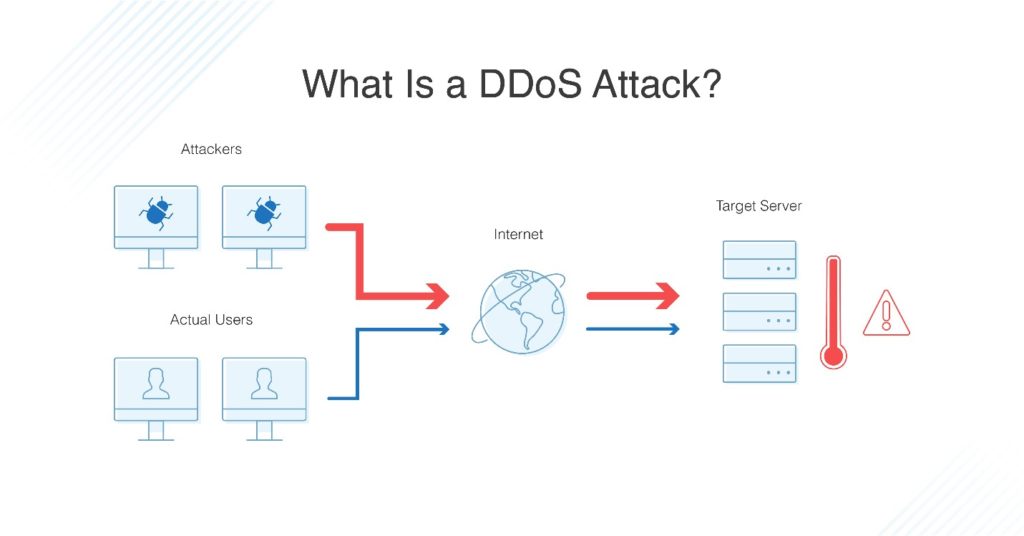
Prevent Ddos Attacks - This involves falsifying the source ip address in data. Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,.
Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. This involves falsifying the source ip address in data.
Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. Here are the most common techniques used with all common types of ddos attacks: This involves falsifying the source ip address in data.
How to stop DDoS Attacks A Complete Guide
Here are the most common techniques used with all common types of ddos attacks: This involves falsifying the source ip address in data. Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,.
Strategies To Prevent DDoS Attacks Bluella
This involves falsifying the source ip address in data. Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,.
Useful Tips to Prevent DDoS Attacks
This involves falsifying the source ip address in data. Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,.
How VPNs Prevent DDOS Attacks
Here are the most common techniques used with all common types of ddos attacks: This involves falsifying the source ip address in data. Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,.
Your AntiDDoS Strategy. Three Ways to Prevent Attacks
This involves falsifying the source ip address in data. Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. Here are the most common techniques used with all common types of ddos attacks:
Denial of Service and DDoS Attacks How to Prevent Them
Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. Here are the most common techniques used with all common types of ddos attacks: This involves falsifying the source ip address in data.
How to Prevent DDoS Attack? What are its Various Types
Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. This involves falsifying the source ip address in data. Here are the most common techniques used with all common types of ddos attacks:
What Is And How To Prevent A DDoS Attack?
Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. This involves falsifying the source ip address in data.
DDoS Protection How To Prevent DDoS Attacks? SolarSpeed
Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. This involves falsifying the source ip address in data.
How to Prevent DDoS Attacks on Critical IT Infrastructure in 2020
This involves falsifying the source ip address in data. Here are the most common techniques used with all common types of ddos attacks: Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,.
This Involves Falsifying The Source Ip Address In Data.
Organizations have many methods they can use to prevent ddos attacks, including increasing bandwidth and server scalability,. Here are the most common techniques used with all common types of ddos attacks: