Man-In-The-Middle Attack Prevention - The most common type of mitm. Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive.
The most common type of mitm. Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive.
The most common type of mitm. Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive.
9 Man In the Middle Attack Prevention Methods to Use Now
Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive. The most common type of mitm.
Man in The Middle Attack PDF Computing Service Industries
The most common type of mitm. Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive.
9 Man In the Middle Attack Prevention Methods to Use Now
The most common type of mitm. Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive.
9 Man In the Middle Attack Prevention Methods to Use Now
Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive. The most common type of mitm.
9 Man In the Middle Attack Prevention Methods to Use Now
Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive. The most common type of mitm.
Man in the middle attack guide and its advantage and prevention Artofit
The most common type of mitm. Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive.
Executing A ManInTheMiddle Attack PDF Information And
Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive. The most common type of mitm.
Man in The Middle Attack PPT by Om Waman PDF Malware Digital Rights
Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive. The most common type of mitm.
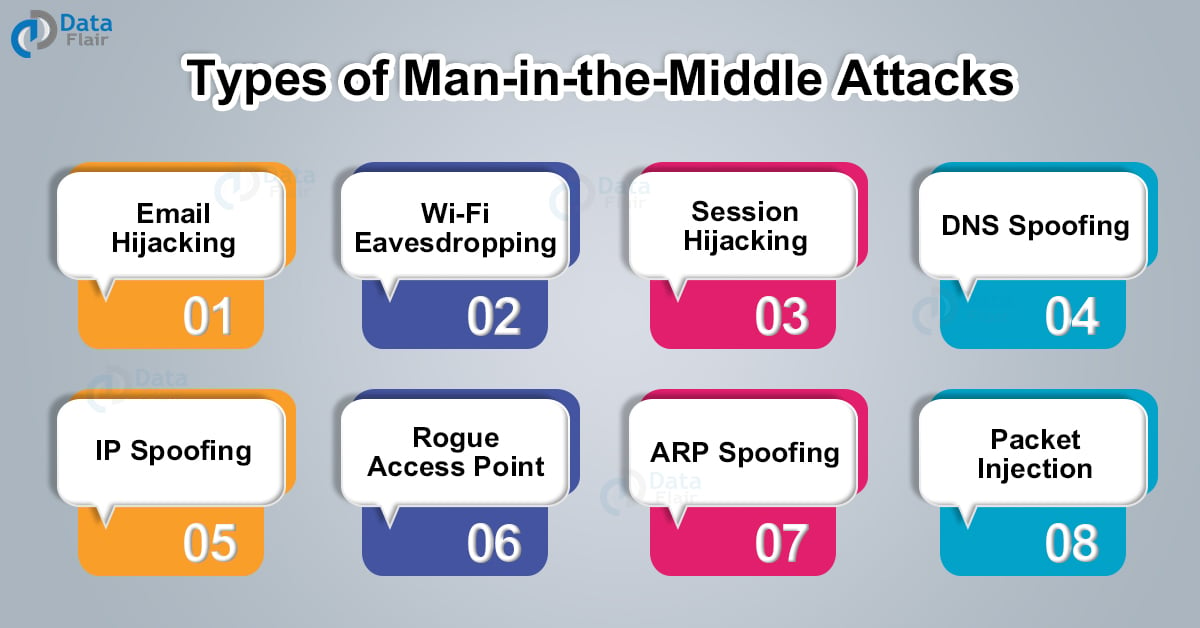
MITM (Man in the Middle) Attack Types and Prevention DataFlair
Monitor the user's online activity or scrape login credentials, credit or payment card information, and other sensitive. The most common type of mitm.
Monitor The User's Online Activity Or Scrape Login Credentials, Credit Or Payment Card Information, And Other Sensitive.
The most common type of mitm.